一、 Vigor的配置:
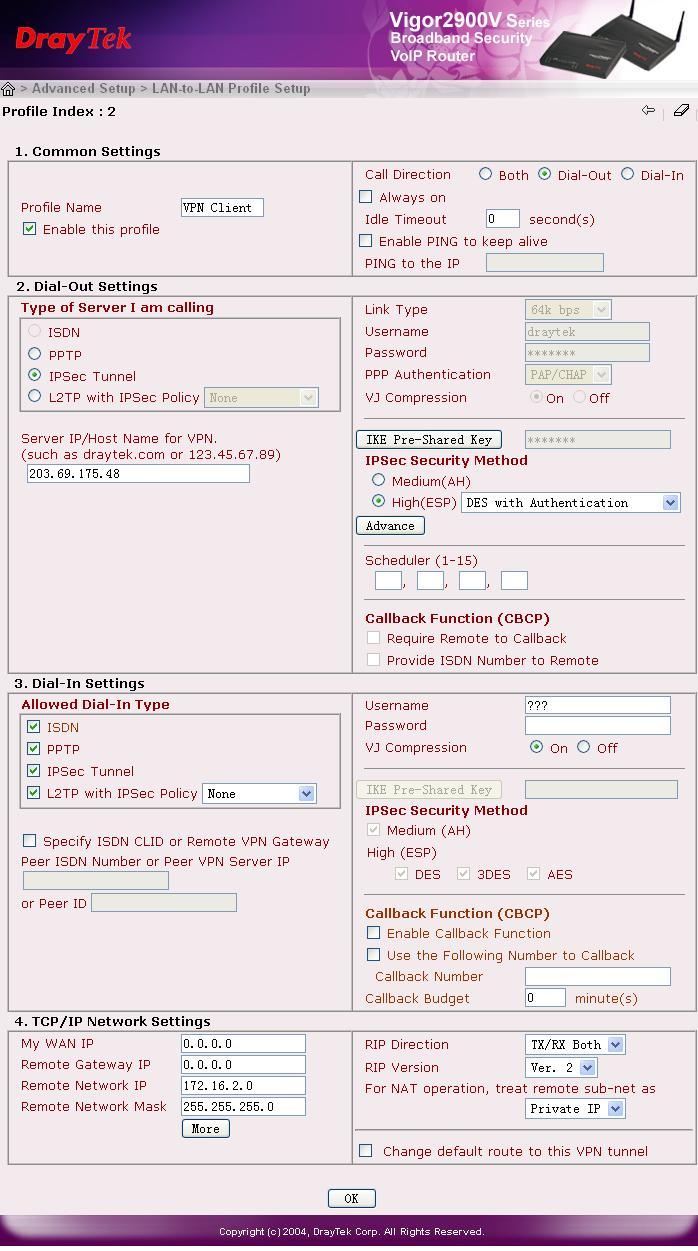
1.基本设置(Common Settings):
a.输入Profile Name.
b. 选择 "Enable this Profile".
c. 选择 Dial-Out,Idle Timeout 选项设为0,这样可以始终维持IPSec隧道的开通直到远端拨入端发出终止命令。如果选择Always on, 那只要连接一中断路由器就会自动重拨。
2. 拨出设置(Dial-Out Settings):
a. 选择IPSec 模式。
b. 输入远端VPN server的IP地址/主机名字。
c. 输入IKE Pre-shared 值。
d. 选择IPSec 安全模式: 高(ESP)。
4. TCP/IP网络设置(TCP/IP Network Settings):
输入远端局域网内网IP地址及其网关。
二、Cisco PIX Settings:
Configuring IPSec with IKE Create a new access list "222" to define the traffic to protect from Head Office's LAN to Branch Office's LAN.
nameif ethernet0 outside security0
nameif ethernet1 inside security100
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
hostname pixfirewall
fixup protocol ftp 21
fixup protocol http 80
fixup protocol h323 1720
fixup protocol rsh 514
fixup protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol sip 5060
fixup protocol skinny 2000
names
access-list 222 permit ip 172.16.2.0 255.255.255.0 192.168.2.0 255.255.255.0
pager lines 24
logging on
interface ethernet0 10baset
interface ethernet1 10baset
mtu outside 1500
mtu inside 1500
ip address outside 210.243.151.181 255.255.255.192
ip address inside 172.16.2.1 255.255.255.0
ip audit info action alarm
ip audit attack action alarm
pdm history enable
arp timeout 14400
nat (inside) 0 access-list 222
static (inside,outside) 172.16.2.0 172.16.2.0 netmask 255.255.255.0 0 0
conduit permit icmp any any
route outside 0.0.0.0 0.0.0.0 210.243.151.190 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h323 0:05:00 si
p 0:30:00 sip_media 0:02:00
timeout uauth 0:05:00 absolute
aaa-server TACACS+ protocol tacacs+
aaa-server RADIUS protocol radius
no snmp-server location
no snmp-server contact
snmp-server community public
no snmp-server enable traps
no floodguard enable
sysopt connection permit-ipsec
no sysopt route dnat
crypto ipsec transform-set Tunnel-ESPDES-MD5 esp-des esp-md5-hmac
crypto map ForInternet 222 ipsec-isakmp
crypto map ForInternet 222 match address 222
crypto map ForInternet 222 set peer 203.69.175.53
crypto map ForInternet 222 set transform-set Tunnel-ESPDES-MD5
crypto map ForInternet interface outside
isakmp enable outside
isakmp key ******** address 203.69.175.53 netmask 255.255.255.255
isakmp policy 22 authentication pre-share
isakmp policy 22 encryption des
isakmp policy 22 hash md5
isakmp policy 22 group 1
isakmp policy 22 lifetime 28800
telnet 172.16.2.10 255.255.255.255 inside
telnet timeout 5
ssh timeout 5
terminal width 80